Terraform State Management: Securing Infrastructure as Code with Azure Blob Storage

In modern DevOps workflows, Terraform plays a central role in automating cloud infrastructure. But there’s one hidden file that holds the keys to your entire environment — the Terraform state file (terraform.tfstate).
If this file is leaked, altered, or lost, it can cause severe issues — from failed deployments to potential data breaches.
At Frankmax Digital, we implemented a secure approach to manage Terraform state using Azure Blob Storage as a remote backend.
Let’s explore how we built it, why it matters, and what best practices every cloud developer should follow.
Why Terraform State File Security Matters
The Terraform state file is like Terraform’s memory — it keeps track of all the resources you’ve deployed.
The Terraform state file is critical because it records the current state of your infrastructure. Storing it locally on a developer’s machine poses significant risks:
- Unauthorized access from compromised systems.
- Accidental deletion or corruption.
- Version conflicts when multiple engineers collaborate.
Using Azure Storage Accounts with Blob Containers as a remote backend eliminates these risks. It ensures state consistency, data encryption, and secure access control through Azure Active Directory (AAD) and Role-Based Access Control (RBAC).
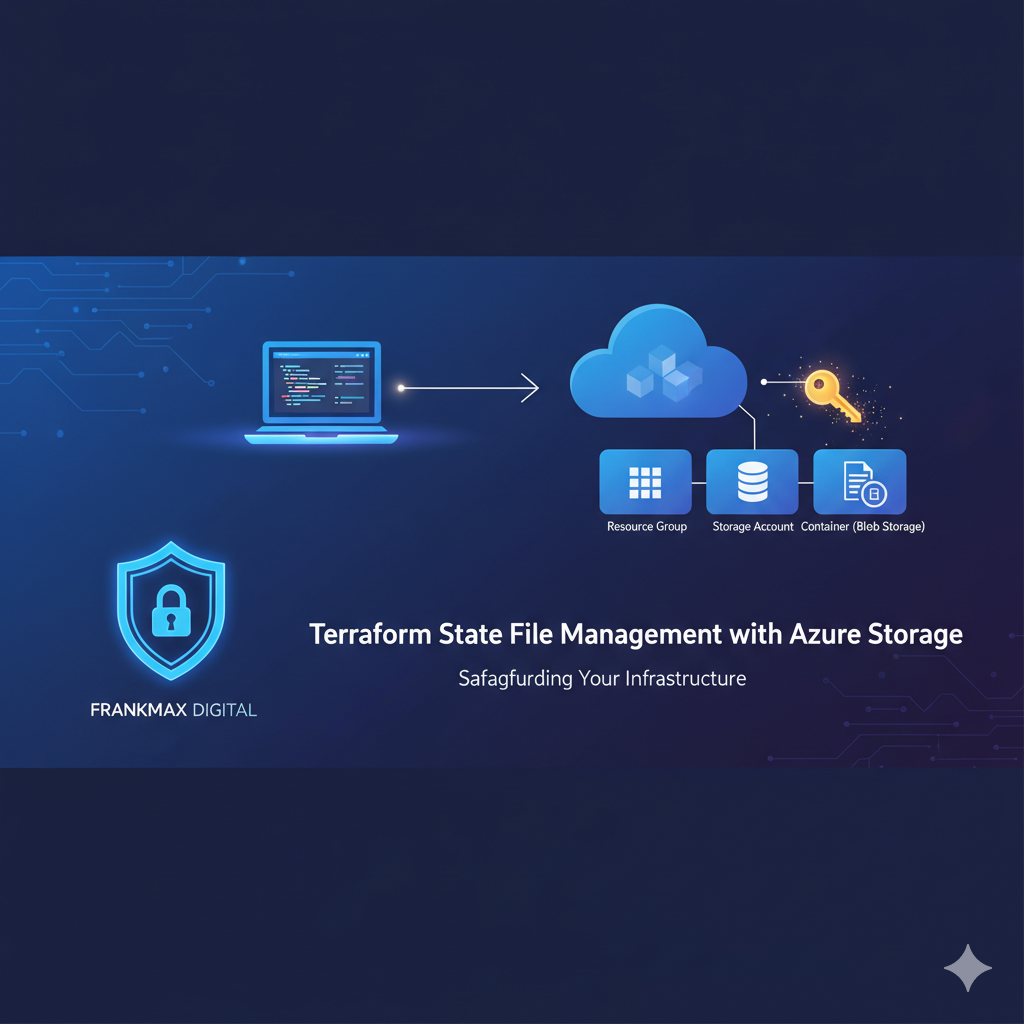
The Secure State Management Workflow
Here’s how we set up Terraform state file security at Frankmax Digital.
Step 1: Backend Setup Script — backend.ch
This Bash script provisions the Azure resources required to host the state file securely.
az account set --subscription d09cc4d9-d3d3-4297-b3ef-a7a33ce803d2
RESOURCE_GROUP_NAME=umbrellacorp-global
STORAGE_ACCOUNT_NAME=kinzal$RANDOM
CONTAINER_NAME=jon727918
# Create resource group
# az group create --name $RESOURCE_GROUP_NAME --location eastus
# Create storage account
az storage account create \
--resource-group $RESOURCE_GROUP_NAME \
--name $STORAGE_ACCOUNT_NAME \
--sku Standard_LRS \
--encryption-services blob
# Create blob container (using your login)
az storage container create \
--name $CONTAINER_NAME \
--account-name $STORAGE_ACCOUNT_NAME \
--auth-mode login
Step 2: Configure Terraform Backend
The Terraform configuration (main.tf) specifies Azure Blob Storage as the remote backend and defines infrastructure resources.
terraform {
required_providers {
azurerm = {
source = "hashicorp/azurerm"
version = "~> 4.8.0"
}
}
backend "azurerm" {
resource_group_name = "tfstate-sushma"
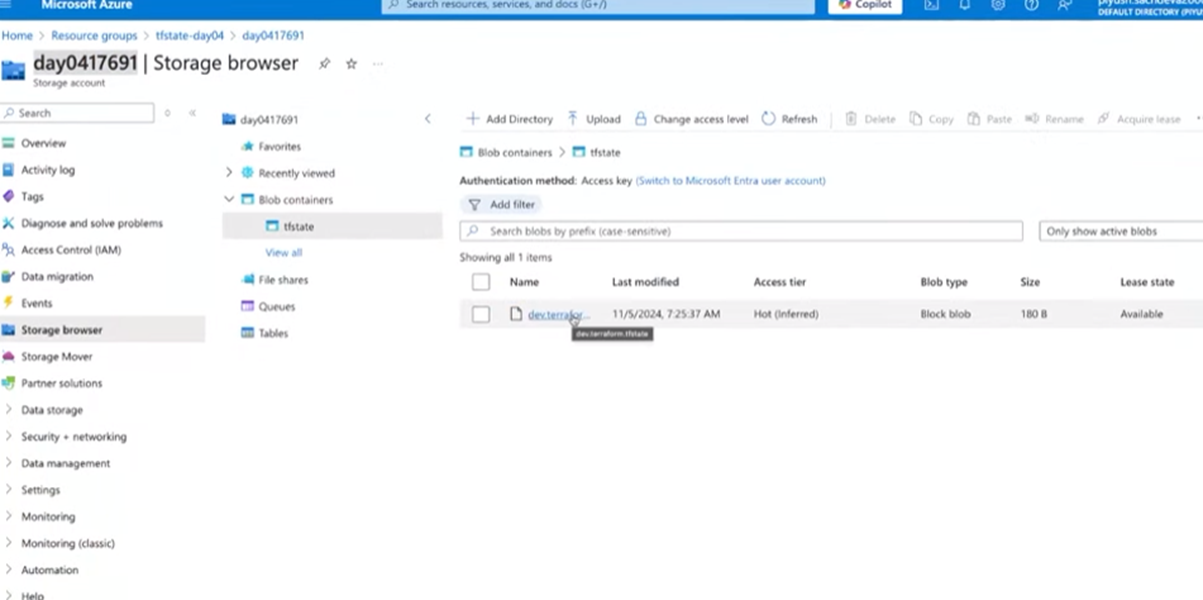
storage_account_name = "day0417691"
container_name = "tfstate"
key = "dev.terraform.tfstate"
}
required_version = ">=1.9.0"
}
provider "azurerm" {
features {}
}
resource "azurerm_resource_group" "example" {
name = "tejas-aircraft-rg"
location = "West Europe"
}
resource "azurerm_storage_account" "example" {
name = "tejasaircraftsa"
resource_group_name = azurerm_resource_group.example.name
location = azurerm_resource_group.example.location
account_tier = "Standard"
account_replication_type = "LRS"
tags = {
environment = "staging"
}
}
Benefits for Enterprise DevOps :
- Centralized State Management — Eliminates local state files and synchronization issues.
- Encryption at Rest and in Transit — Blob-level encryption ensures data security by default.
- Azure AD + RBAC Integration — Enables fine-grained, role-based access control for DevOps teams.
- Consistency and Collaboration — A shared remote backend prevents state drift and merge conflicts.
- Auditability — Blob access logs and Azure Monitor integration support full traceability for compliance.
Conclusion
Securing Terraform state files is essential for maintaining the integrity, scalability, and compliance of infrastructure automation. By leveraging Azure Blob Storage as a remote backend, Frankmax Digital ensures:
- Robust state management
- End-to-end encryption
- Seamless collaboration across DevOps teams
Following these best practices will help safeguard your Terraform workflows and strengthen your enterprise cloud security posture.